select the best answer. which of the following are breach prevention best practices
Which of the following are breach prevention best practicesAccess only the minimum amount of PHIpersonally identifiable information PII necessaryLogoff or lock your. Do you have strong password policy and is it being adhered to.
Phishing Prevention Best Practices
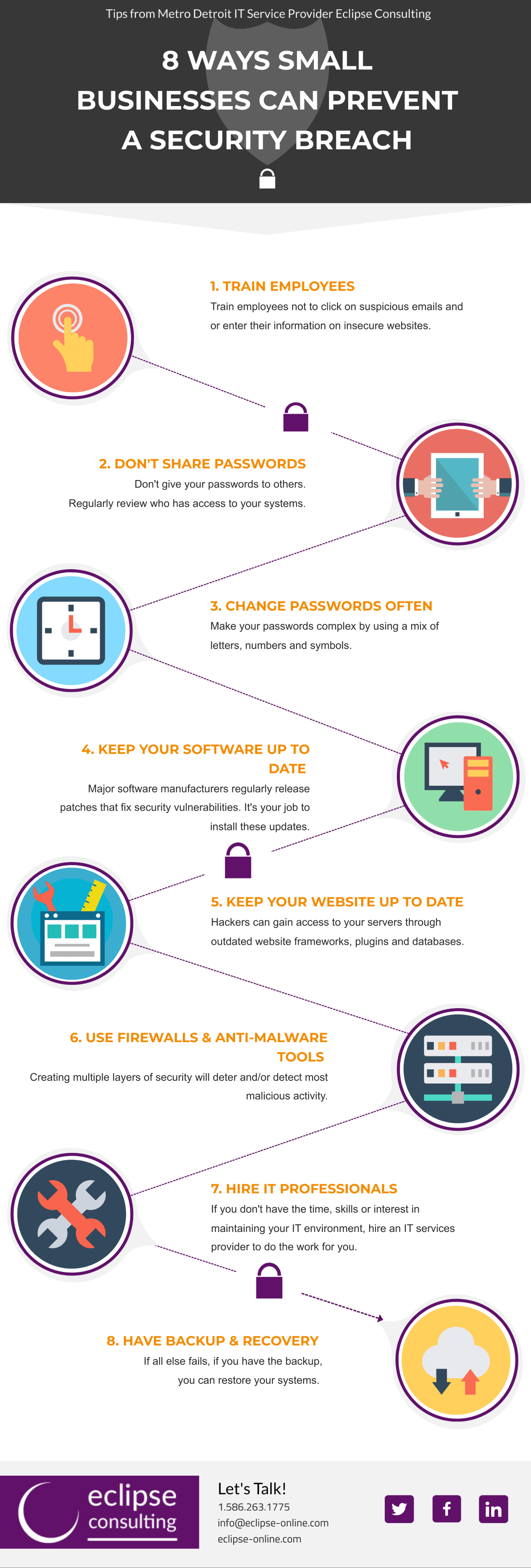
Implementing encryption standards and backup policies to decrease risks and make sure that software is up.
. These 15 best practices can be used to reduce the likelihood of a data breach and help you respond more quickly to an attack. D communicating a purchase order to a supplier. Physical measures including policies and procedures that are used to protect electronic information systems and related buildings and equipment from natural and environmental.
2 Which of the following are breach prevention. Which of the following are breach prevention best practices. Misdirected communication containing PHI or PIIC.
True Select the best answer. Logoff or lock your workstation when it is unattended. Select the best answer.
Promptly retrieve documents containing PHIPHI. Access only the minimum amount of phipersonally identifiable information pii necessary. Developing the IRP will help the IT staff of the company to control the data breach incidents.
Which of the following are common causes of breaches. And privacy officials select reasonable and appropriate. 12 charts show the.
Best practices for breach prevent are. Select the best answer. Data breaches are an everyday reality in a connected business.
Identity sensitive data collected stored transmitted or processes. Best practices for breach prevent are. Select The Best Answer.
Identify areas that store transmit collect or process. Which Of The Following Are Breach Prevention Best Practices - Fit Food Fashion. Top 4 Human Errors In Cyber Security How To Prevent.
Which of the following are breach prevention best practices All of the above. Which of the following are breach prevention best practices Saturday June 11 2022 Edit. Remediation Accessed N PHI transmitted orally PHI on paper PHI.
The following are high-level best practices for preventing breaches. Which of the following are breach prevention best practices. Which of the following are breach prevention best practices.
All of this above. Companies that leveraged artificial intelligence machine learning. 30 Best Practices for Preventing a Data Breach.
Create Strong Policies Strong Passwords. Which of the following are breach prevention best practices. Invest in security automation.
Making weak passwords can be a reason for Data. Promptly retrieve documents containing PHIPHI from the. Which of the following are breach prevention best practices.
30 Best Practices for Preventing a Data Breach. Promptly retrieve documents containing PHIPHI from the printer.

7 Key Steps To Investigate A Data Breach With Checklist Ekran System

What Is A Data Breach How To Prevent One

30 Best Practices For Preventing A Data Breach Securityscorecard

Best Practices For Securing Sensitive Data In Aws Data Stores Aws Database Blog

Best Practices For Writing Secure Java Code Coralogix

Top 9 It Security Threats And How To Address Them It Security

Preventing Hipaa Data Breaches Case Studies And Best Practices

Best Practices For Securing Sensitive Data In Aws Data Stores Aws Database Blog

7 Data Loss Prevention Best Practices Expert Explains Purplesec

What Is Data Security Definition Planning Policy And Best Practices Spiceworks 1

Which Of The Following Are Breach Prevention Best Practices All Of The Above You Course Hero

Fraud Prevention Strategies Tactics And Best Practices

Data Loss Prevention Next Steps

9 Data Security Best Practices For Your Enterprise Loginradius Blog

What Is A Data Breach How To Prevent One

5 Ways Big Companies Protect Their Data Endpoint Protector

30 Best Practices For Preventing A Data Breach Securityscorecard

California Data Security Breach Reporting Requirements Termsfeed

7 Data Loss Prevention Best Practices Expert Explains Purplesec